I was really surprised to see how easy it is to configure Ansible Tower/AWX to use Microsofts Azure AD as an external Identity Provider.
Not only does this simplify user management in Ansible Tower within our organisation but also opens the possibility of providing “Ansible as a Service” to our customers who are hosting workloads in our data centres. By permitting them to log into our Tower host using their own corporate credentials, they can enjoy all the benefits of automation without having to run their own dedicated instances of Ansible Tower.
To enable single sign on with Azure AD in Tower, you will need System Administrator privileges on the Tower host, and an account in your Azure tenant which has the necessary permission to create a new App Regstration in Azure AD (See Microsoft Docs)
Start by navigating to settings -> authentication in Tower
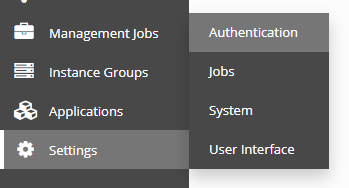
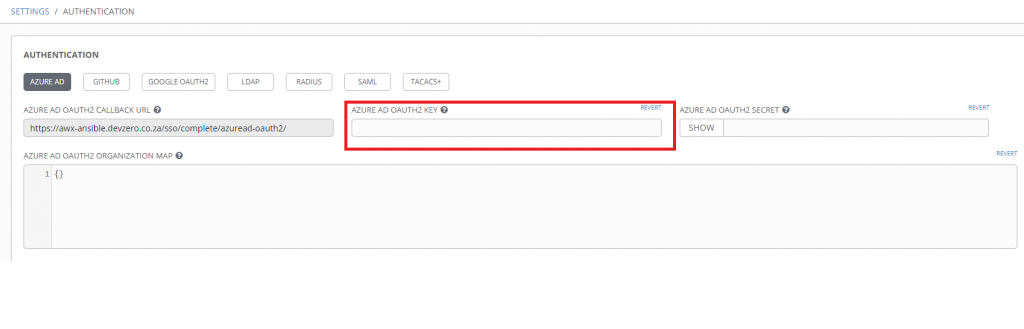
Take note of the callback URL on the Azure AD tab in Tower.
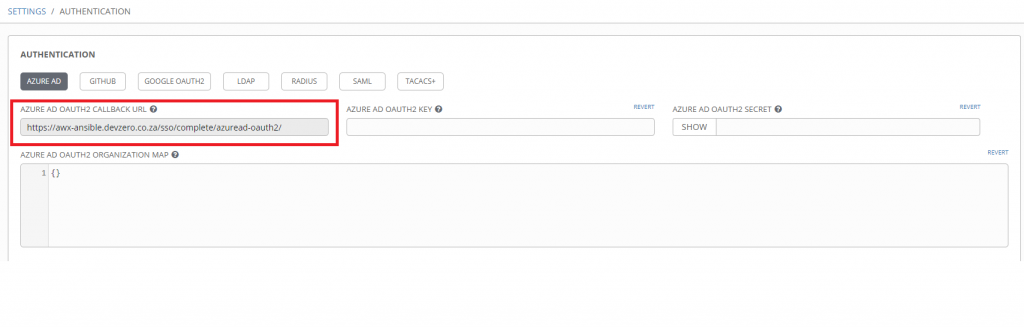
Next, log into the Azure portal and navigate to Azure Active Directory -> App Registrations -> New Registration
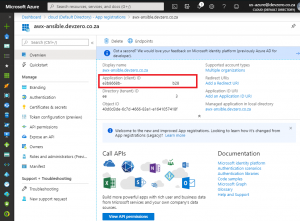
Provide a descriptive name for the App Registration, in this case I’m using awx-ansible.devzero.co.za.
If you want organisations other than your own to be able to login to your Tower instance select
“Accounts in any organizational directory (Any Azure AD directory – Multitenant)” from the Supported account account types and then save the configuration by clicking register.
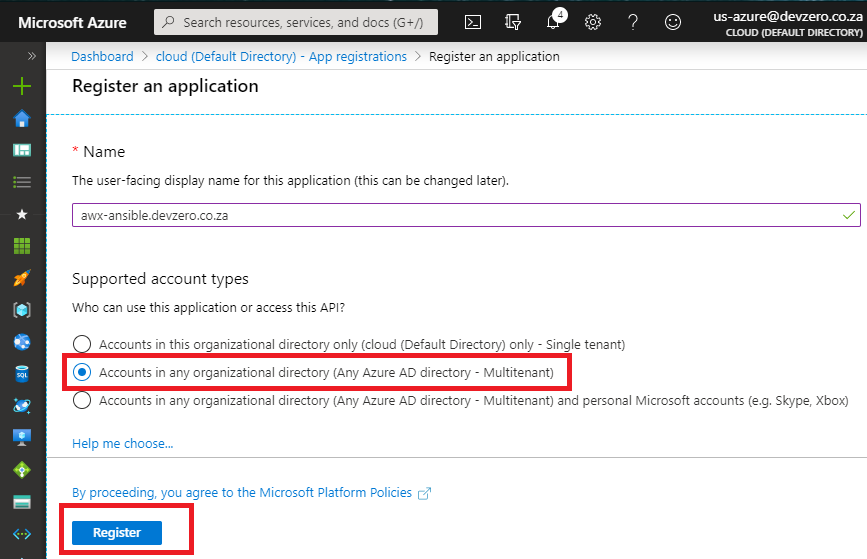
Once the application is registered, take note of Application (client) ID you’ll use this value in the “Azure AD OATH2 KEY” field back in Tower.
On the App Registration page in the Azure portal Navigate to Authentication and paste the “Azure AD OAUTH2 Callback URL” provided by Tower in the Redirect URL field and then click Save.
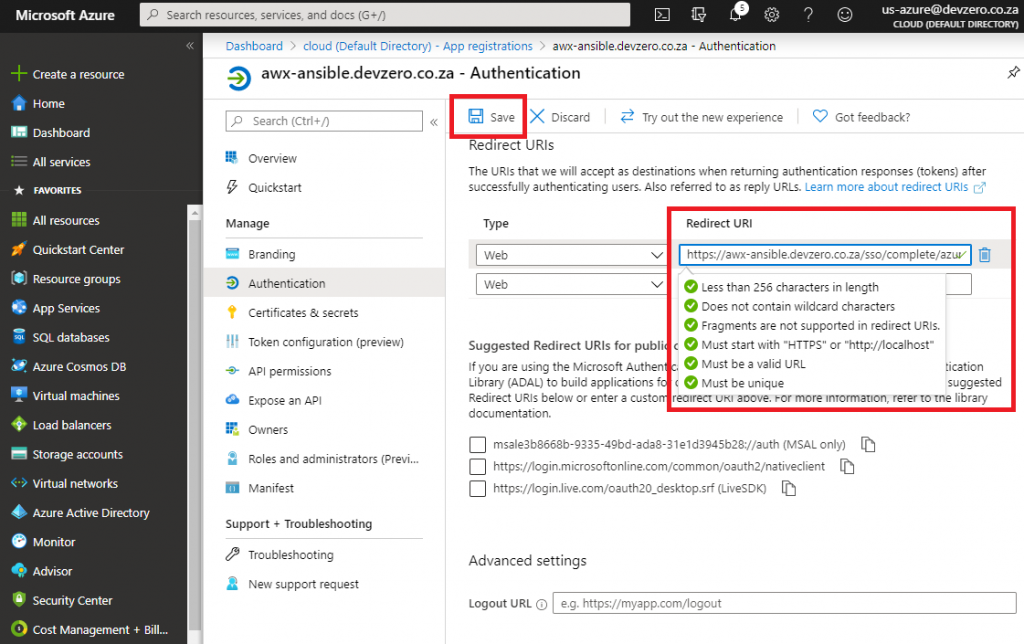
Staying on the App Registration page, navigate to Certificates & secrets, click New client secret, provide a meaningful description and define how long the key should be valid and click add.
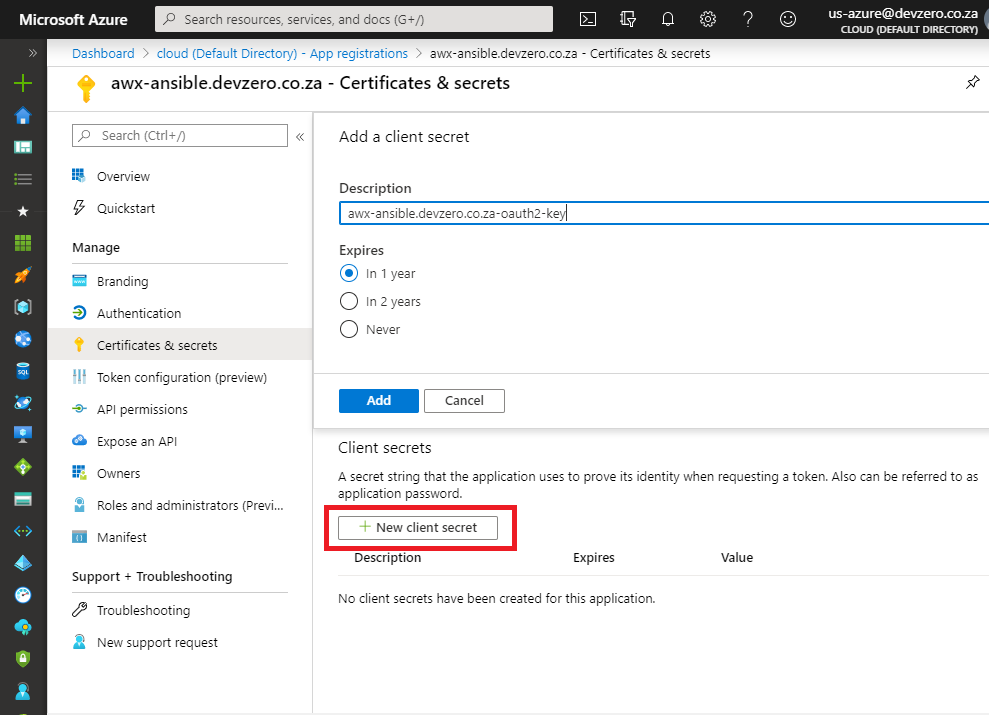
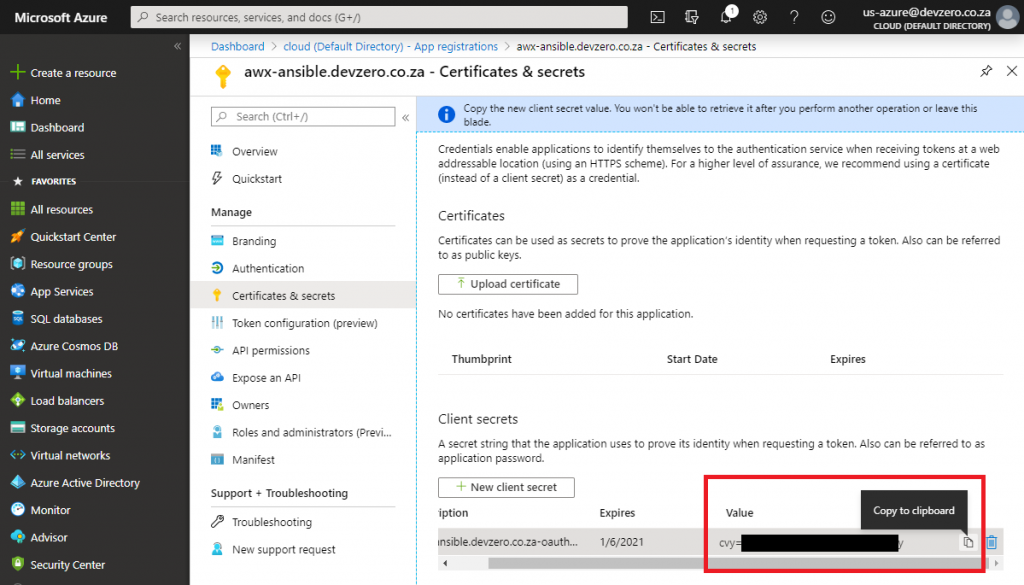
After the key is generated, copy the key value and paste it into the Azure AD OAUTH2 SECRET field in Tower. Do not navigate away from this blade until you’ve stored the value as you will not be able to see it again.
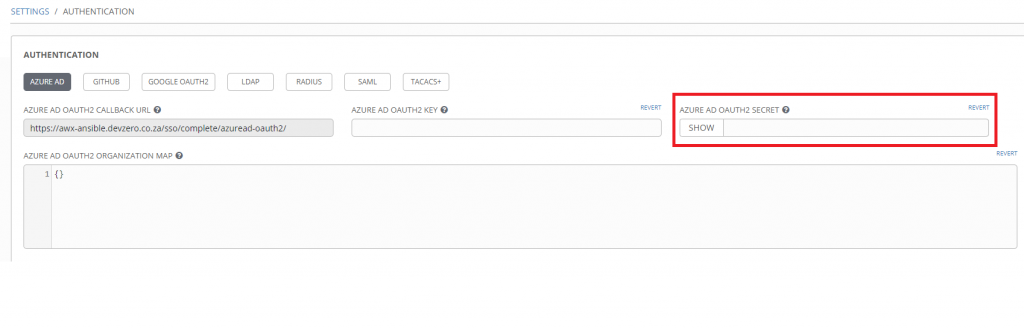
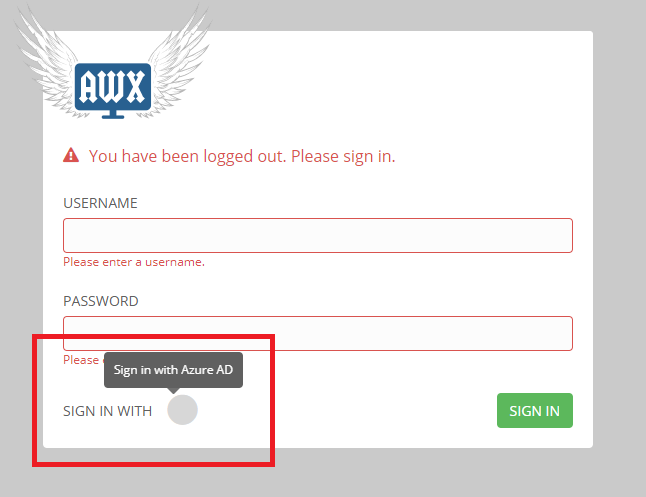
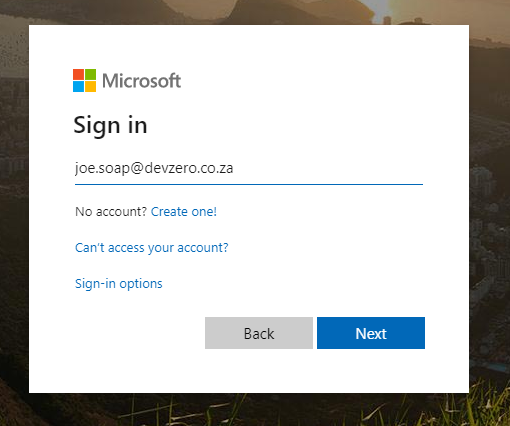
At this stage users should now be able to log into Tower with Azure AD. On the Tower login screen, click Log in With Azure AD below the login form. You’ll be redirected to the Microsoft login page. Continue to authenticate using your Azure AD Credentials.
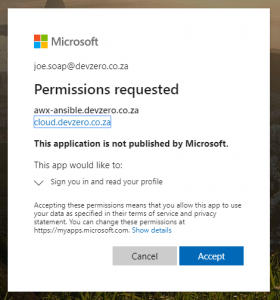
For the authentication to be successful, Azure AD may ask you to permit the App Registration (in this case awx-ansible.devzero.co.za) to read information from your Azure AD profile, click accept.
The user should now be logged into Tower with their Azure AD identity, but they will be a regular user with no permissions to any Tower objects. As a Tower administrator, you will now be able to assign them to Organisations or Teams and assign the necessary permissions to resources like Inventories, Templates, credentials etc.



One thought on “Ansible Tower/AWX Single Sign on With Azure AD”
Hello sean,
Thank you for the article! Qns for you please. Where do you specify the tenant id? We’ve followed the instructions but it failed when we tried to sign in. App id was what we set but the tenant id is definitely not ours. Would love to have your advice. Thanks!