In this post, I look at capturing network packets at the Hypervisor layer instead of inside the Virtual machines or at the network layer.
I found myself in this situation when I was asked to troubleshoot an issue where I didn’t have access to the VM nor the network device. I did however own the ESXi host, so seeing as though I was literally man in the middle, I had to figure out the most logical way to do it.
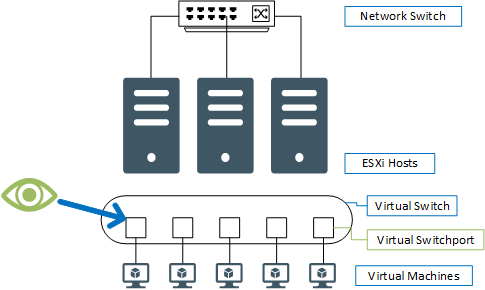
I have 3 ESXi hosts configured with a Virtual Distributed Switch. I could simply capture all the packets on the interfaces that connect the ESXi host to the physical network, but I would see all traffic for all the virtual machines. Instead I’ll capture the packets at the Virtual Switch port layer. This way I don’t have to filter out the noise from the other VMs.
First I identify the Virtual switchport number of the virtual interface plugged into the VM.
[root@vmware2:~] net-stats -l
PortNum Type SubType SwitchName MACAddress ClientName
33554434 4 0 vSwitch0 00:10:e0:8b:28:34 vmnic0
33554445 3 0 vSwitch0 00:10:e0:8b:28:34 vmk0
33554485 5 9 vSwitch0 00:0c:29:56:f9:bd research01.devzero.co.za
33554486 5 9 vSwitch0 00:0c:29:6e:02:6b research02.devzero.co.za
To capture packets on the interface plugged into a VM named research02.devzero.co.za. I can simply run this command:
pktcap-uw --switcport %SWITCHPORT_NUMBER%
In reality however, the default behaviour of pktcap-uw will only capture inbound packets to the selected interface. So I’ll run two different captures simultaneously as background jobs.
To do so I’ll use the –dir option with a value of 0 for ingress traffic and a value of 1 for egress traffic. Packet captures printed out to the terminal are useless, so I’ll write them to a file using the -o option.
pktcap-uw --switchport 33554486 --dir 0 -o /var/tmp/33554486_in.pcap & pktcap-uw --switchport 33554486 --dir 1 -o /var/tmp/33554486_out.pcap &
To stop the capture issue this command.
kill $(lsof |grep pktcap-uw |awk '{print $1}'| sort -u)
This will result in two files. To analyse them in wireshark, I’ll need to combine them into a single capture file.
I’ve installed wireshark on my windows machine, so I’ll download the two capture files from the ESXi host and use mergecap from the wireshark installation directory to combine the two files.
C:\Program Files\Wireshark>mergecap.exe -w c:\Users\10\Downloads\33554486_merged.pcap c:\Users\10\Downloads\33554486_in.pcap c:\Users\10\Downloads\33554486_out.pcap